Vector Fingerprint Scanner Locked Icon. Fingerprint Scanner Locked Simple Icon In Flat Style With Long Shadow. Security Concept Icon Royalty Free SVG, Cliparts, Vectors, And Stock Illustration. Image 62156756.
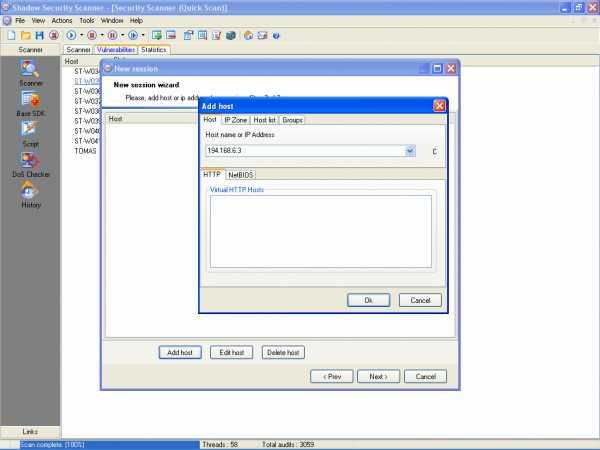
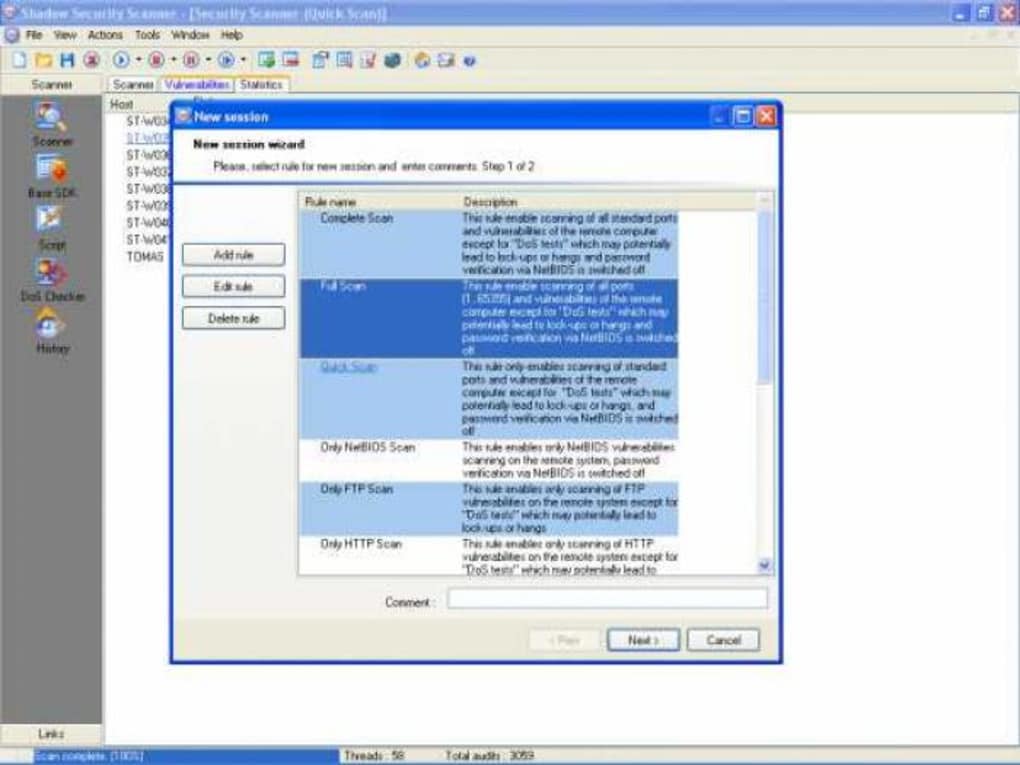
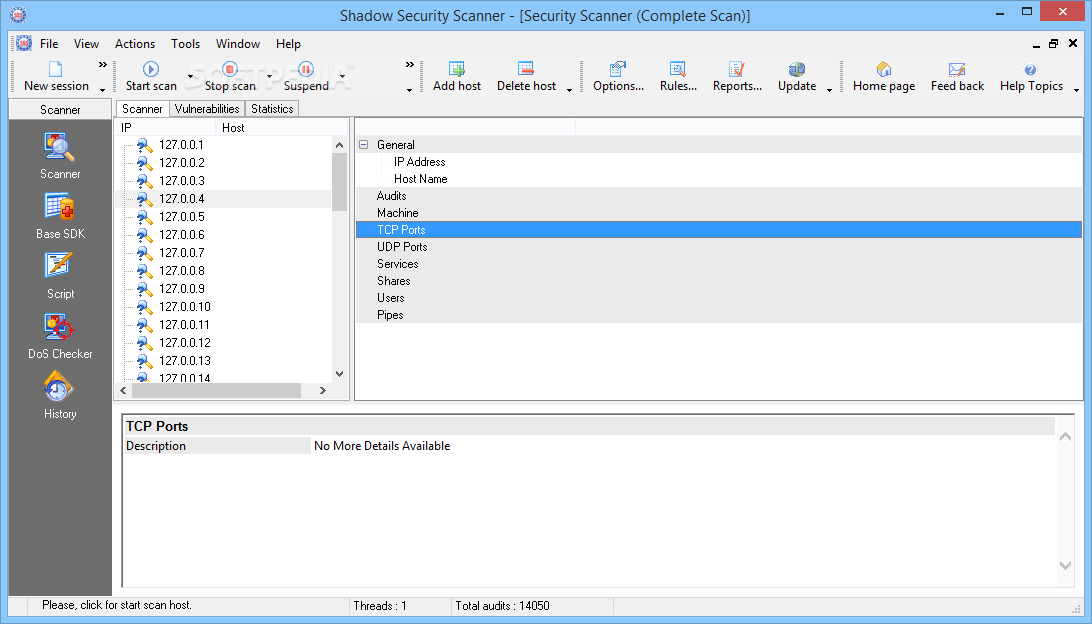
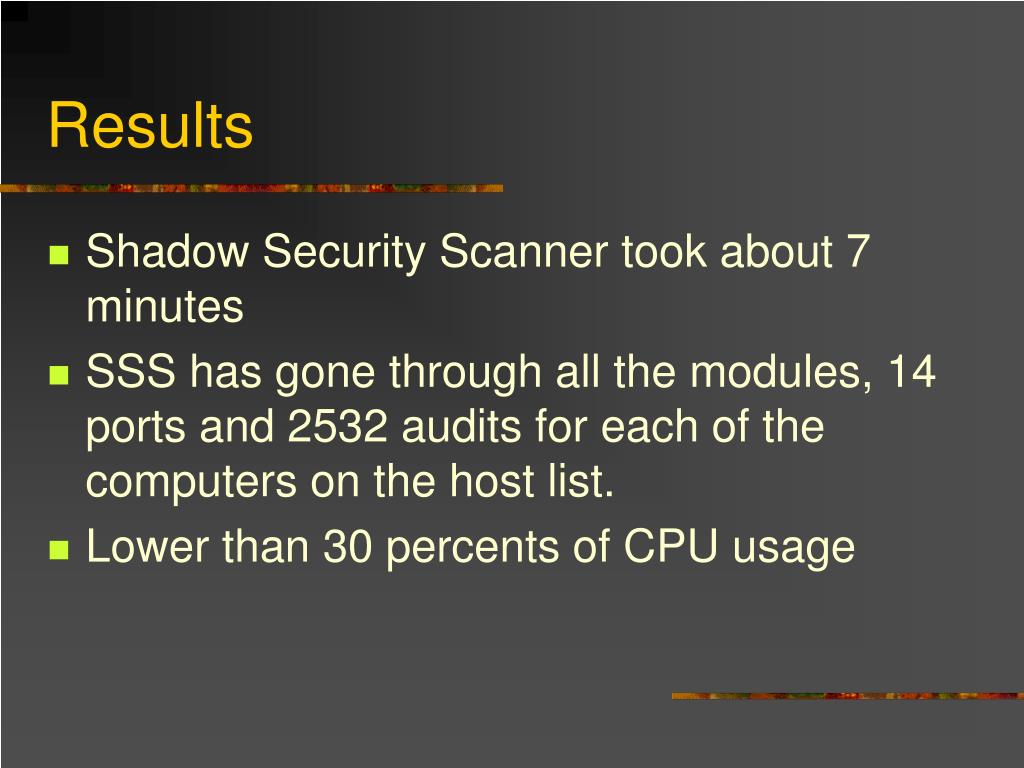
Shadow Database Scanner Download - It provides a secure and prompt detection of security system holes
Signaling portal metal detector flat design long shadow glyph icon. Airport security scanner with person inside. Vector silhouette illustration Stock Vector Image & Art - Alamy
X-ray baggage scanner flat design long shadow glyph icon. Airport security. Weapon detected in handbag. Vector silhouette illustration Stock Vector Image & Art - Alamy